Most of the time when a customer is asking for a SIEM, really they just want a way to detect threats across their environment, and they think SIEM is the only way to achieve this. It’s not, and for many customers, Sophos MTR makes much more sense.
A few customers I’ve spoken with recently are considering buying a SIEM or an SIEM service. With a bit of probing about what they’re trying to achieve, we’ve got them interested in Sophos MTR as an alternative.
Security Incident and Event Management systems, or SIEM, have been around for a long time. Many IT managers are under the misconception that SIEM is the only way to get a complete view of what’s happening on their network.
An SIEM takes alert data from firewalls, endpoints, switches and other sources and tries to make sense of these alerts to detect attacks. However, this alerts-based approach is slow, unreliable, and prone to “alert fatigue.” A lot of time and effort is required to manage, configure, and tune an SIEM. Even if the SIEM detects an attack, someone still needs to respond to the threat. And don’t forget, an SIEM doesn’t replace endpoint protection. Our customers will still need Intercept X on their servers and PCs.
Sophos Managed Threat Response (MTR) offers a better option for your customer to respond to threats across their network. If your customer is already using Sophos Intercept X and Endpoint Detection and Response (EDR) there’s no additional software to install, configure, or tune. MTR augments Sophos’ Intercept X and EDR with osquery to build a searchable SQL database of every computer OS in your environment.
The Sophos MTR team regularly executes scheduled queries on every endpoint to capture useful data to detect and investigate threats. Live queries can also be executed to return information immediately from the endpoint for threat hunting, incident response, and investigations.
The MTR team reviews details on detections, endpoint-related information, and checks to see if the detection was seen on other endpoints. They can see detailed information about what was executed, allowing for further investigation into the pid, parent process, and relevant hashes.
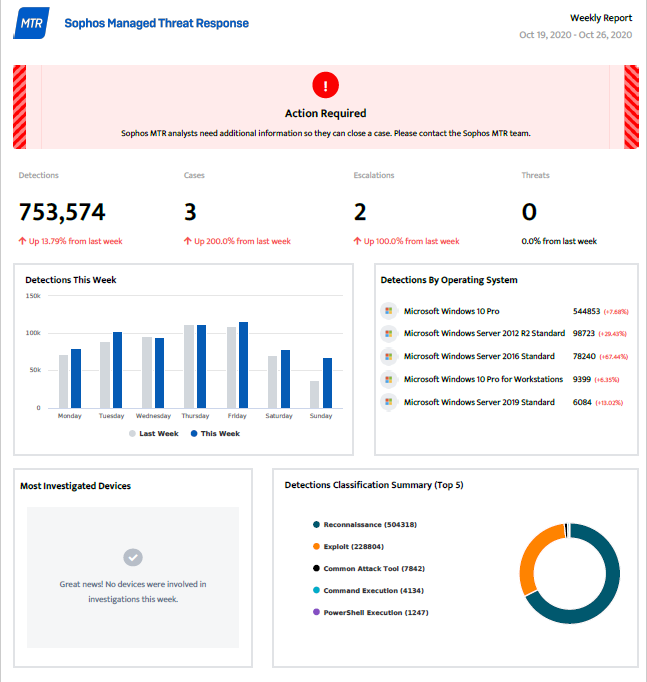
Furthermore, unlike with SIEM, the MTR team will respond, 24 hours a day, 7 days a week. They can:
- Change configurations to manage an active threat, including adjusting threat policies, enabling EDR/MTR on unprotected devices, and adjusting exclusions
- Use Sophos Central’s isolate host functionality to limit a compromised asset’s exposure
- Block files by SHA256 within an environment to prohibit malicious content from running
- Initiate a system scan
- Block a specific website or IP address through web control
- Block a specific application through application control
- Use a Live Terminal for direct access to the host
So, next time you hear your customer mention SIEM, ask them: who’s going to respond to the SIEM alert at 3 a.m. on a Sunday morning?
Instead, offer them Sophos MTR, the better option to detect attacks on sensitive data assets and respond to incidents before they become a breach. Even at 3 a.m. on a Sunday morning.