Sophos unveils major advancements to Sophos Intercept X Advanced for Server with XDR, enabling Sophos Partners to build long term security strategies with customers running Linux server and container workloads, whether on-premises, in the datacenter or public cloud. These new server workload protection capabilities provide a lightweight solution for the detection of exploits and anomalous behaviors in customer environments before attacker can get a foothold.
Through the integration of Capsule8 technology, which was acquired by Sophos in July 2021, Sophos Cloud Workload Protection can now identify attacks as they happen within Linux operating systems. Achieved by leveraging analytics around attacker behavior, from initial access (including application and system exploitation) to privilege escalation, defense evasion, data collection, exfiltration and many others. It provides powerful and lightweight visibility into on-premises, data center, hybrid and multi-cloud Linux hosts and containers. Securing them from advanced cyberthreats.
Securing Linux Infrastructure
Whether your customers are running physical servers, host virtual machines or containers, Sophos protects Linux infrastructure now and as it evolves with high impact workload protection that’s low impact on performance.
It’s ideal for SOC teams that need powerful threat hunting and remediation capabilities as well as DevSecOps teams that need deep insight into their mission critical workloads with minimal impact to performance. Sophos will provide multiple deployment options – a lightweight agent today, managed from Sophos Central, a single management console to seamlessly move between threat hunting, remediation and management. A Linux threat sensor fine-tuned for performance will soon follow, using APIs to integrate runtime threat detections into your existing threat response tools. Both options will provide maximum visibility of workloads with minimal impact on performance.
A sample of Sophos cloud-native detections include:
- Container escapes: Identifies attackers escalating privileges from container access to move across to the container host
- Cryptominers: Detects program names or arguments commonly associated with cryptocurrency miners
- Data destruction: Alerts that an attacker may be trying to delete indicators of compromise that are part of an ongoing investigation
- Kernel exploits: Highlights if internal kernel functions are being tampered with on a host
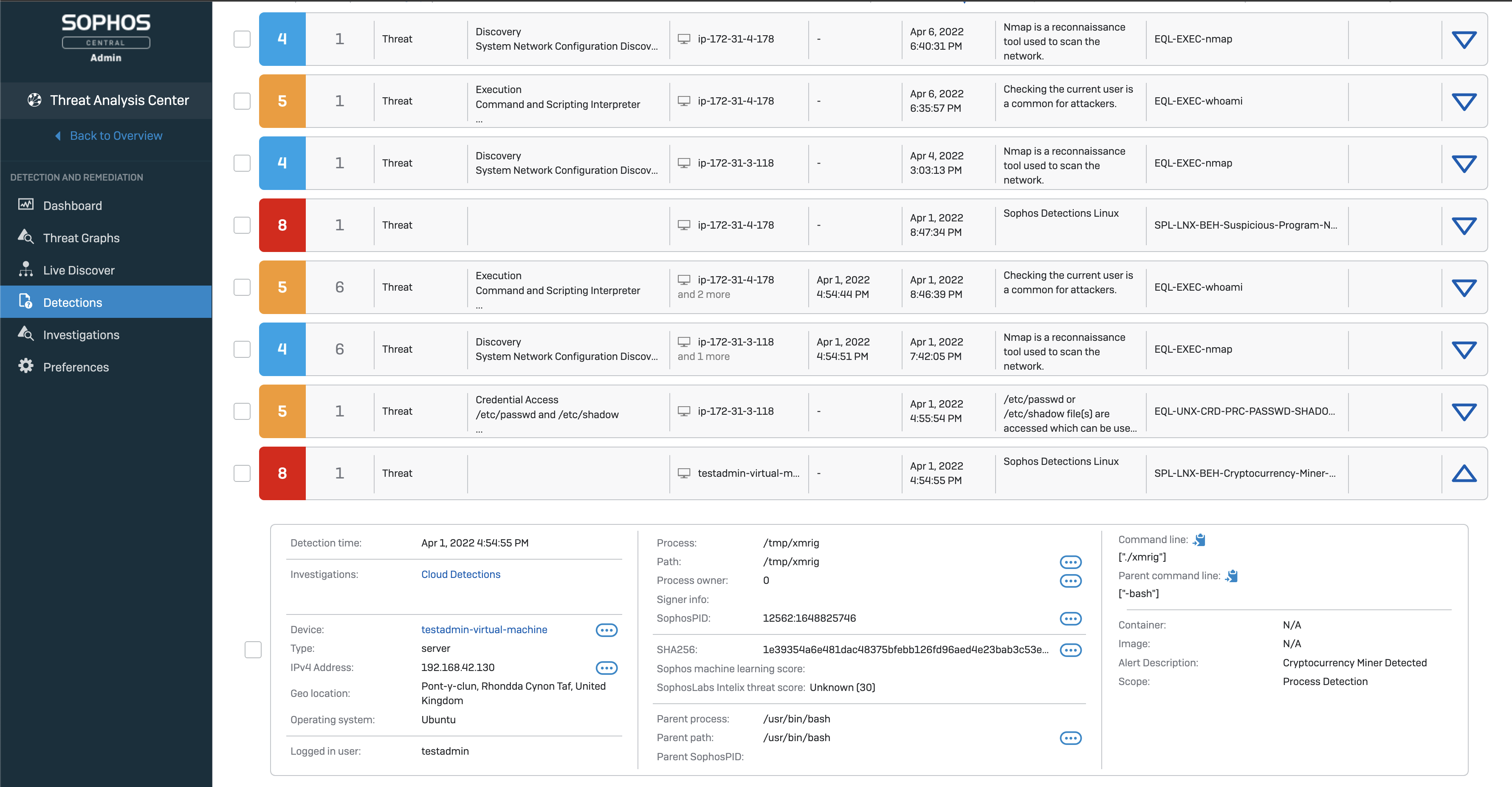
Minimize Your Time to Respond to Linux Threats
Helping organizations stay ahead of the curve of threat behavior, Sophos Partners have a range of options available to take advantage of these new advancement in Linux protection. Firstly, through Intercept X for Server with XDR. Here, all behavioral and exploit runtime detections are immediately funneled into the Sophos XDR data lake. These host and container threat detections are automatically converted into an investigation, with an AI-prioritized risk score for each detection. Scores are then color-coded by risk level. This enables your own Managed SOC team, or your customers’ own team, to quickly identify where they should focus to increase efficiency. Integrated Live Response further establishes a secure command line terminal to hosts for rapid remediation.
When you would prefer assistance to provide around the clock monitoring and incident response, then Sophos Managed Threat Response, the Sophos MDR service, can also work in partnership with your partner security team, or directly with the customer, monitoring on-premises or cloud environments 24/7/365 to respond to Linux security incidents as they happen for total peace of mind.
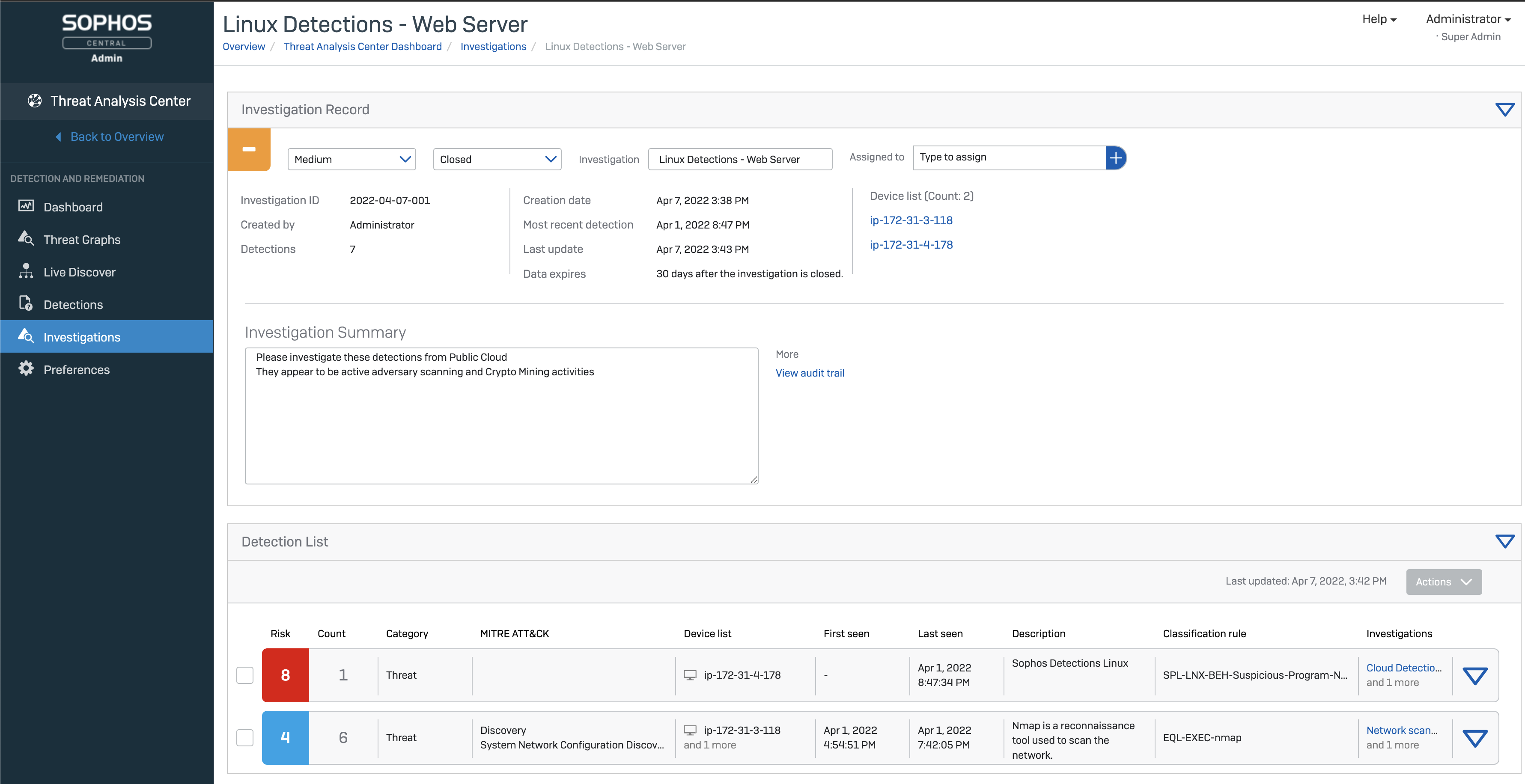
Secure Your Cloud Growth
Sophos Cloud Workload Protection seamlessly integrates with the Sophos Adaptive Cybersecurity Ecosystem, which underpins the entire Sophos portfolio of solutions. It’s connecting Sophos’ range of Cloud Native Security Platform capabilities including cloud workload protection, Cloud Security Posture Management (CSPM), Kubernetes Security Posture Management (KSPM), container image scanning, Infrastructure-as-Code scanning, Cloud Infrastructure Entitlements Management (CIEM), and cloud spend monitoring to maintain visibility, security, and compliance and meet the evolving needs of your customers and security practice.
Whether your customers are running infrastructure on premises, in the cloud or datacenter, host and container today, or tomorrow. Sophos secures applications and data across their entire hybrid cloud footprint from a single console with one flexible agent. To find out more and try Sophos Cloud Workload Protection free for 30-days, visit sophos.com/cwpp