You may have seen the acronym AMA used on Reddit and various other social platforms out there. Normally, it’s used for developers and people of interest that host a round of open questions, like “Question Time,” but more intense! AMA, in those scenarios, means “ask me anything.” Well with the latest version of EDR (v3), we give you the power to “ask machines anything.” Currently, we support Windows endpoints, Windows Server, and Linux machines. Mac support will be added soon too.
EDR v3 uses OSQuery to enable us to poll devices for information. The great thing about OSQuery is that it tries to be OS agnostic; the same queries work on different platforms. The slightly odd thing about it, is that it’s all based around SQL. Personally, I’ve not had much need to be throwing SQL queries about since I left tech support nearly eight years ago. I guess that’s going to have to change now!
If you’re like me, and your SQL-fu is a little … aged, you might want to start with the built-in queries. Thankfully, there are loads of them, and the majority have come from our elite MTR team (who are constantly running threat-hunting activities on customer devices).
Since there are a lot of queries in there already, it can be a little daunting at first. But, my aim with this article is to help you get a leg up with using it.
Getting Started – Selecting Devices
Jump into the Threat Analysis Center > Live Discover. From here, you’ll get a list of all EDR-protected devices, use the filters to narrow down the list, and select those devices you wish to learn more about:
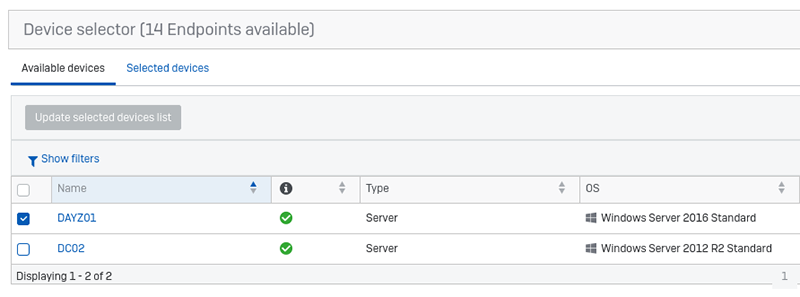
Tick the boxes, and then click ‘update selected devices list.” It’s a little like shopping online: you select the items you want to buy and then they appear in the basket, or in our case the “selected devices” basket. Click on “selected devices” to see what you have in the basket. If this is your first time, I would recommend that you just select a single device for starters; some of the queries we can grab a lot of data.
Scroll down to the Query section and we’ll have a run through it:
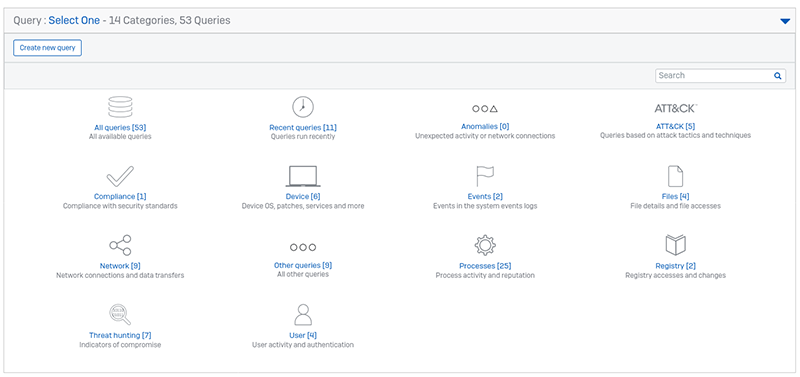
Getting Started – Queries
There are load of queries in here, arranged in subcategories to help you find the ones you are after. You can also search for a query and create your own.
So, what can we use this for?
Threat Hunting
Let’s start off with a look at threat hunting using EDR v3 as the base. As mentioned above, our EDR system uses OSQuery. In fact, at the time of writing, we are using version 4.2. The schema can be found here: https://osquery.io/schema/4.2.0. It gives a list of all the native OSQueries available, but of course we have supplemented these native queries with our own.
The Sophos queries can be found on the community forums.
Generally speaking, the native OSQueries will look at live, current data, like running processes or the value of a defined registry key. The Sophos journal tables on the other hand can query our data recorder which records for about 30 days, capturing all processes, registry values, file actions, and network connections.
Truly there is a lot of data that can be obtained, but thankfully you don’t have to go it alone. We’ve created a large collection of useful queries for you, and there is an ever-increasing number of them on the community forum.
Here’s an example of the query “New processes that run automatically” which shows various load points used by software to run when a machine is booted. Can you spot the suspicious entry?
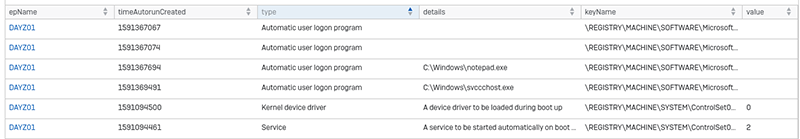
All results can be exported from the console, and they are even cached for up to two hours. You can get back into a previous query from Threat Analysis Center > Dashboard > Recent Live Discover queries.
With this query it’s easy to find malicious or suspicious load points for software, but there are so many more queries to play with. Here’s a few of my personal recommendations:
- New processes that run automatically
- PowerShell events suspected of using encoded or encrypted data
- Processes listening on ports
- Scheduled tasks
- Remote authentication attempts
Auditing and Other Information
It’s true, EDR was designed with threat hunting in mind. But since it can access so much information from the devices, it can be used for all manner of other data collection.
In the list of pre-made queries there are plenty that have nothing to do with threat hunting and can be easily used to aid an IT team in finding useful information about their machines. A couple of handy ones that spring to mind are:
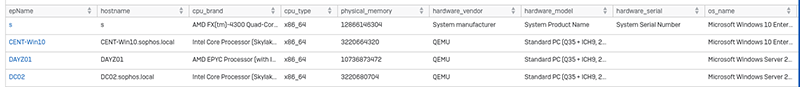
Hardware and Operating System Details
Shows the hardware information, like the CPU type, amount of RAM, hardware vendor, and other information too.
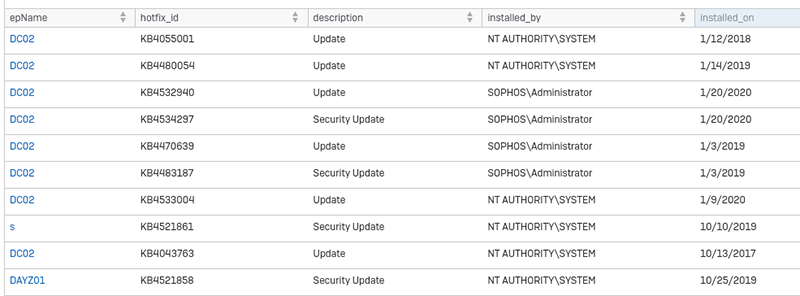
Patches Applied
Shows the installed patches on devices, as well as who triggered the installation and when it happened. Very handy if you want to know whether all machines have installed their Windows updates or not.
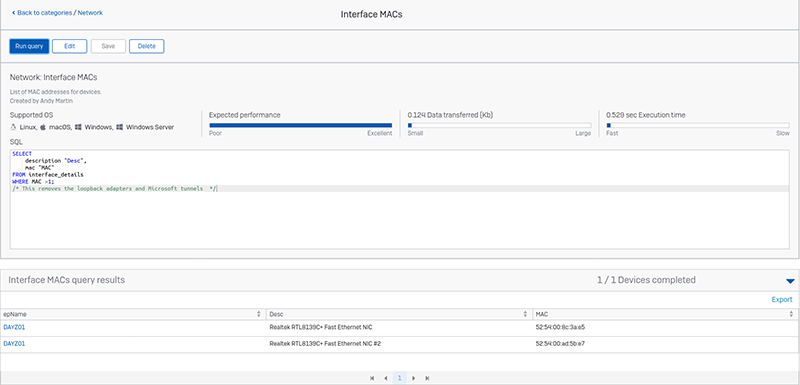
Interface MACs
OK, I’m cheating. This one doesn’t exist normally, I created it. It’s a very simple query. Just click on “create new query,” give it a name and a description, and then paste the following into the query box:
SELECT
description “Desc”,
mac “MAC”
FROM interface_details
WHERE MAC >1;
/* This removes the loopback adapters and Microsoft tunnels */
When you are ready, click “run query” and beyond a list of your MAC addresses. It should work on all supported operating systems.
Useful Resources
Below is a list of places I’ve found useful whilst creating queries. Hopefully, you’ll find it handy too:
A Note From Andy
I hope this encourages you to get playing with EDR v3. It’s a very powerful tool that allows admins to “ask machines anything.”