Multiple exploits have been found in one of Dell’s Windows kernel drivers. The five related bugs, which may lead to escalation of privileges, denial of service, or information disclosure, are collectively classified as CVE-2021-21551.
Dell issued a patch for these vulnerabilities on May 4th, 2021 and we recommend you apply it earliest opportunity.
The bugs go all the way back to 2009, and Dell’s official list of affected products stretches for many pages. As a result, the challenge for IT teams is identifying whether your organization is impacted by this issue, the scope of that impact, and how to focus your time and remediation efforts appropriately.
Query with Sophos EDR
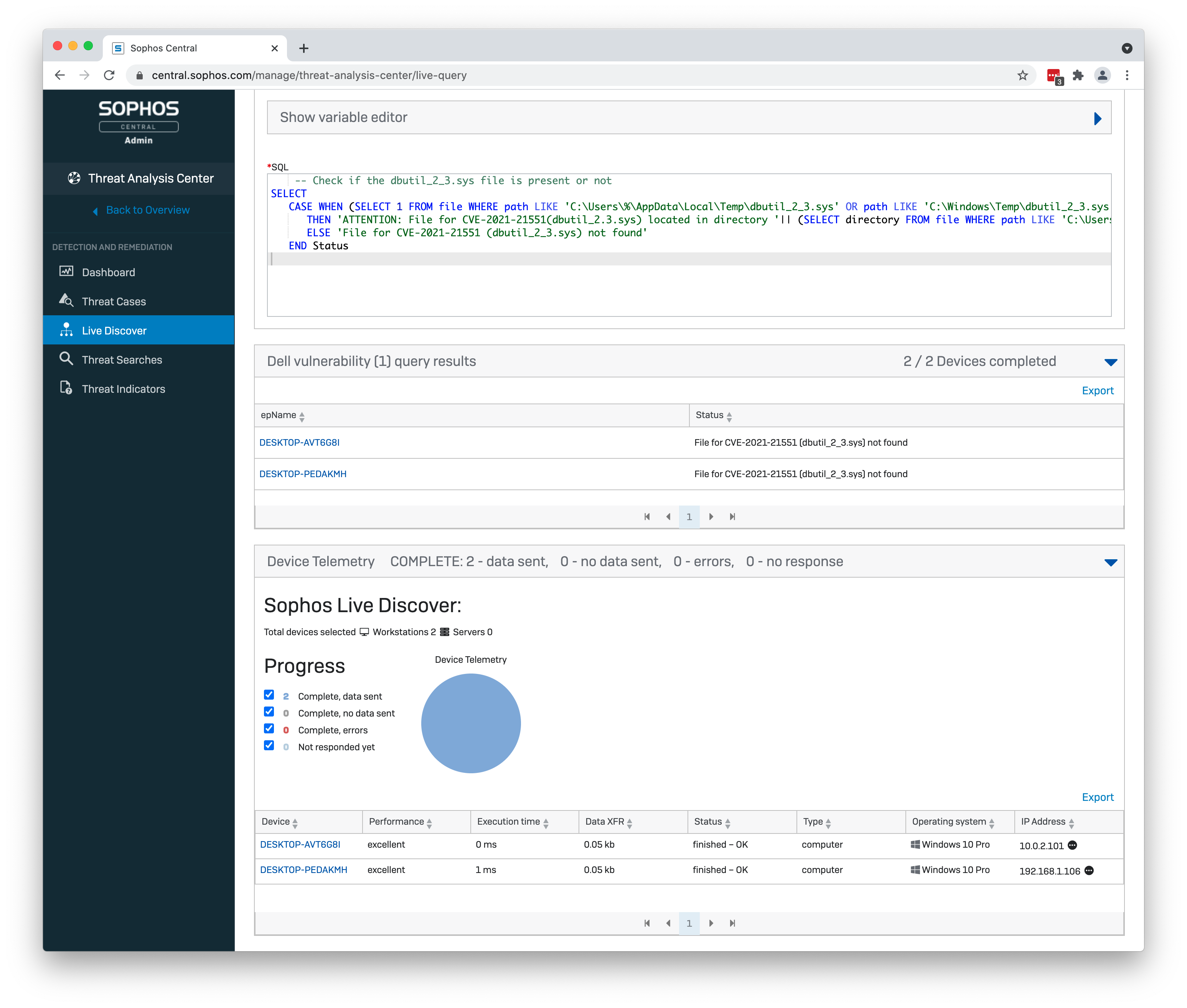
Sophos Endpoint Detection and Response (EDR) makes it easy to identify whether you have the file associated with this vulnerability on a device, and how many devices have that file. This allows you to focus remediation efforts and quickly address the issue.
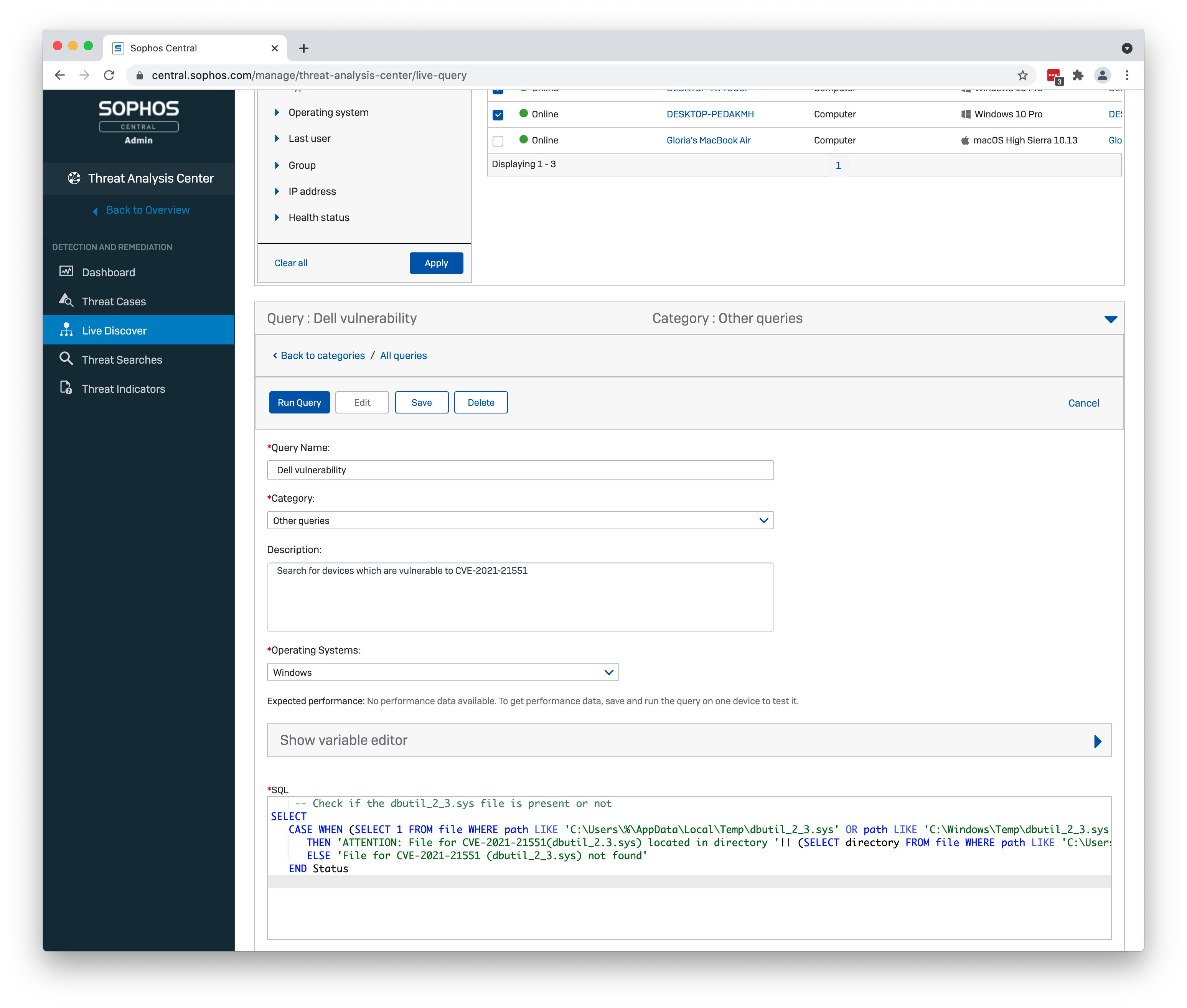
We have created a custom query to identify which endpoints across your estate are vulnerable and require your attention. It also confirms if an endpoint is not vulnerable.
Go to the Threat Analysis Center in Sophos Central, select Live Discover and create a new query.
Cut and paste the query below:
-- Check if the dbutil_2_3.sys file is present or not SELECT CASE WHEN (SELECT 1 FROM file WHERE path LIKE 'C:\Users\%\AppData\Local\Temp\dbutil_2_3.sys' OR path LIKE 'C:\Windows\Temp\dbutil_2_3.sys') = 1 THEN 'SYSTEM REQUIRES ATTENTION: File for CVE-2021-21551 (dbutil_2.3.sys) located in directory '|| (SELECT directory FROM file WHERE path LIKE 'C:\Users\%\AppData\Local\Temp\dbutil_2_3.sys' OR path LIKE 'C:\Windows\Temp\dbutil_2_3.sys') ELSE 'File for CVE-2021-21551 (dbutil_2_3.sys) not found' END Status
Run the query across your estate.
Remediating impacted devices
Dell has provided instructions for manually removing the affected kernel driver, which it advises will be found in one of two places:
- C:\Users\%USERNAME%\AppData\Local\Temp\dbutil_2_3.sys
- C:\Windows\Temp\dbutil_2_3.sys
If you are nervous about removing system files by hand, Dell has published a download page with an automatic driver remover.
Learn more
For more information on the vulnerability and how it can be exploited, read the Sophos Naked Security article.
Sophos EDR is available for both endpoints and servers and is included in Intercept X subscriptions. You can run it for free, for thirty days:
- Existing Sophos customers using Sophos Central can activate a free trial directly within their management console. Simply select Free Trials at the bottom of the left hand navigation bar.
- Anyone not using Sophos can start a free trial via our website.