Today, we’re proud to launch another major advancement to Sophos Cloud Workload Protection, with new Linux and container security capabilities available via API to integrate with your customers’ SecOps and DevOps systems.
Performance Without Friction
When uptime is your customer’s number one requirement, security tools must be lightweight and integrate into your existing workflows to prevent risk and optimize application performance.
For agile organizations with an expanding production environment, achieving that balance, while getting comprehensive protection, is no easy task. Especially if you’re running an increasingly dispersed technology stack which may include physical servers, virtual machines, and containers, deployed on-premises or in the cloud.
Enter Sophos new Linux Sensor which is able to proactively detect sophisticated attacks across your entire Linux production environment, pointing you to the true attacks that require attention. This will allow you to maximize uptime and avoid overloaded hosts – problems that are caused by traditional security tools.
Multiple Deployment Options
Preannounced in early April 2022, Sophos Linux and container security enhancements now provide multiple deployment options. The first, a lightweight agent managed from the Sophos Central management console, and now the Linux Sensor, fine-tuned to provide runtime detections and ideal for highly latency sensitive workloads.
Sophos Central management – This lightweight Linux agent gives security teams the critical information they need to investigate and respond to behavioral, exploit, and malware threats in one place. Monitoring the Linux host, this deployment option allows teams to manage all their Sophos solutions from a single pane of glass, seamlessly moving between threat hunting, remediation and management.
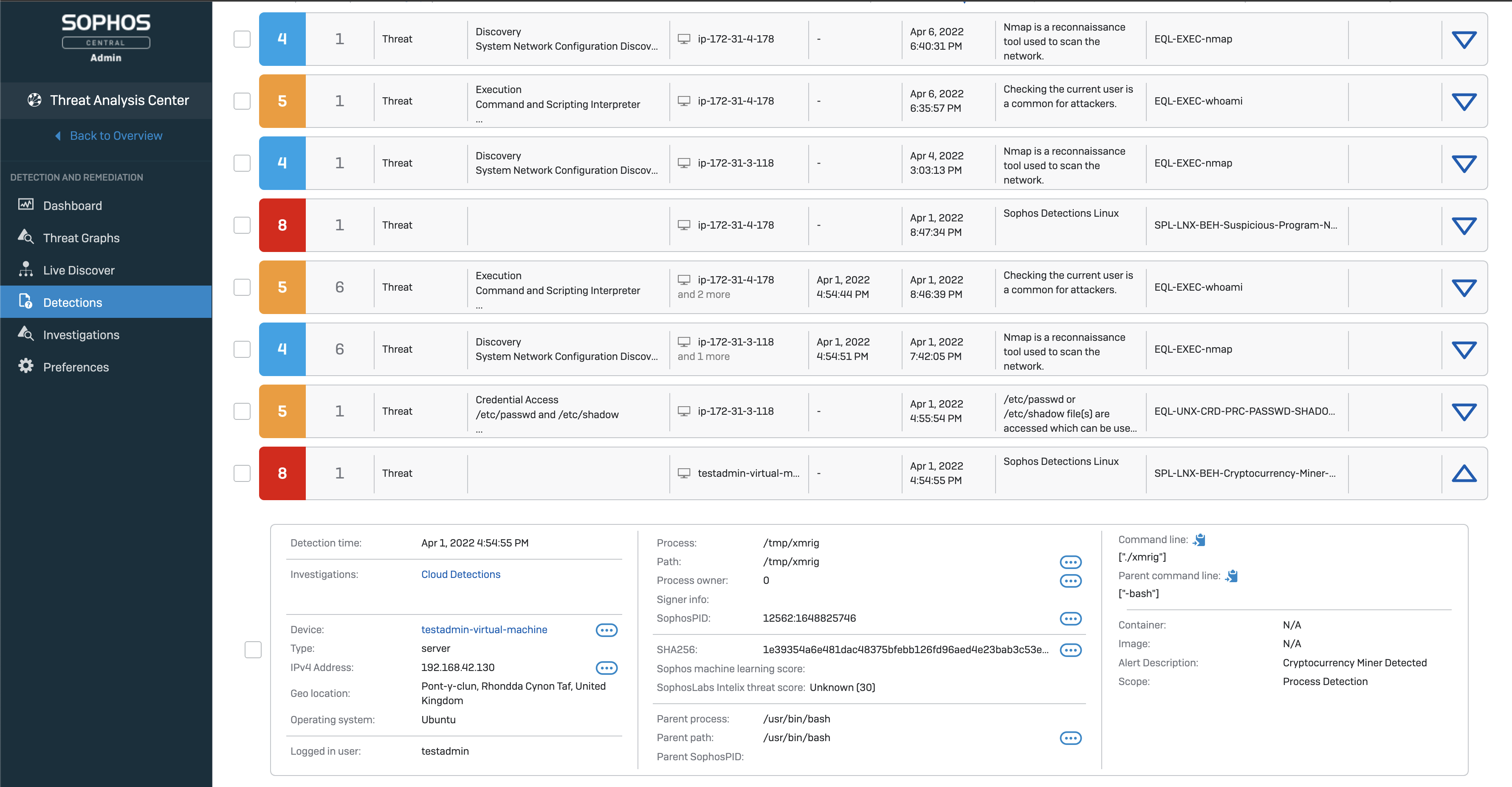
New API Integration – Sophos Linux Sensor is a highly flexible deployment option that is fine-tuned for performance. The Linux sensor uses APIs to integrate rich runtime threat detections, in host or container environments, with your own or your customers existing threat response tools.
Providing access to the full set of runtime detections, including additional detections for application and system exploitation, the sensor delivers a greater level of control that’s ideal for teams needing the granularity to create custom rule sets containing only those runtime behavioral detections needed to meet a specific security monitoring use case.
A sample of Sophos Linux and container detections include:
- Container escapes: Identifies attackers escalating privileges from container access to move across to the container host
- Cryptominers: Detects program names or arguments commonly associated with cryptocurrency miners
- Data destruction: Alerts that an attacker may be trying to delete indicators of compromise that are part of an ongoing investigation
- Kernel exploits: Highlights if internal kernel functions are being tampered with on a host
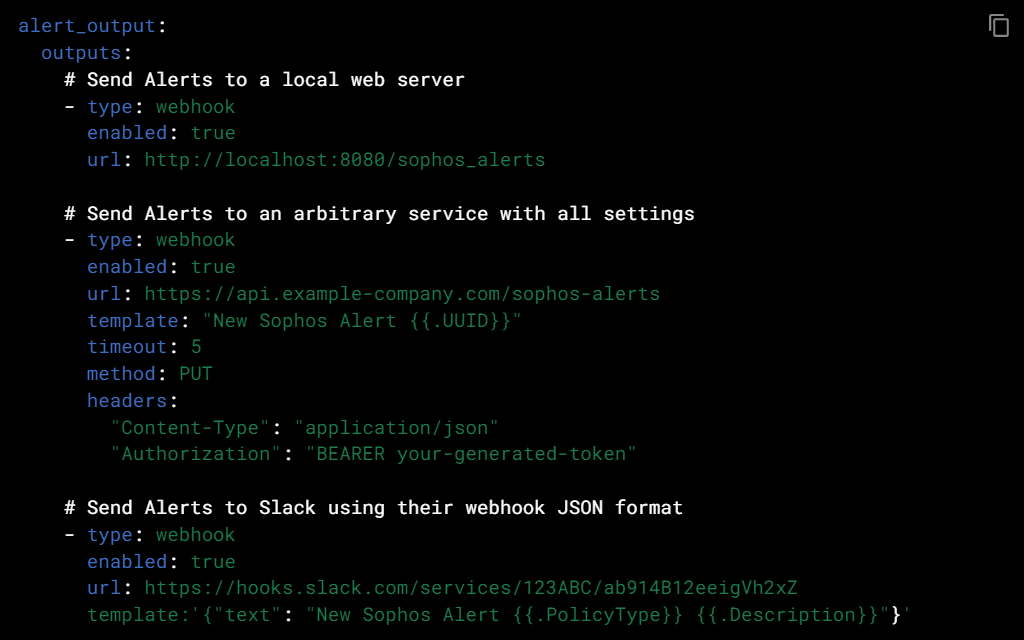
Easy Integration with existing SecOps and DevOps systems
The Sophos Linux Sensor was designed with flexibility in mind to make it easy for customers to consume host and container behavioral and exploit runtime detections alert data in a way that fits in naturally with your existing workflows. The API makes it simple to integrate that data into your existing SecOps and DevOps systems, tools, and processes. Including SIEMs like Splunk, or sending alerts using a webhook to Amazon S3, Amazon Simple Queue Service, Google Cloud Storage, ELK, and Azure Storage to be picked up for analysis.
For those who want a management console, with integrated threat hunting, investigation and remediation capabilities built in, you can choose to install the Sophos Linux agent. This enables partners or customers to manage protection from Sophos Central, our single management console that unifies Sophos’ range of hybrid-cloud security platform capabilities; including Sophos Cloud Workload Protection, Sophos Cloud Security Posture Management, Kubernetes security posture management, container image scanning, infrastructure-as-code scanning, cloud infrastructure entitlements management, and cloud spend monitoring, to ensure visibility, security and compliance.
To find out more about Sophos Cloud Workload Protection visit sophos.com/cwpp
For existing partners looking to activate the Linux Sensor contact sophoslinuxsensor@sophos.com to get started.