With the launch of Sophos Wireless v2.3, you and your customers now have access to many user-enhanced features.
What’s New:
- Sync Sec: Option to activate Synchronized Security separately for Endpoint and Mobile (UEM)
- Sync Sec: Option to create Managed Device only SSIDs
- Sync Sec: Customization of URL whitelist for red security heartbeat/walled garden status
- User ID: User identity shown in device list for some authentication types
Note: All Synchronized Security features are only supported on the APX Series.
Synchronized Security in Wireless is a great way to open up new cross-sell opportunities, now also alongside XG Firewall in accounts where synchronized security is already being used (as long as Wireless is managed in Sophos Central).
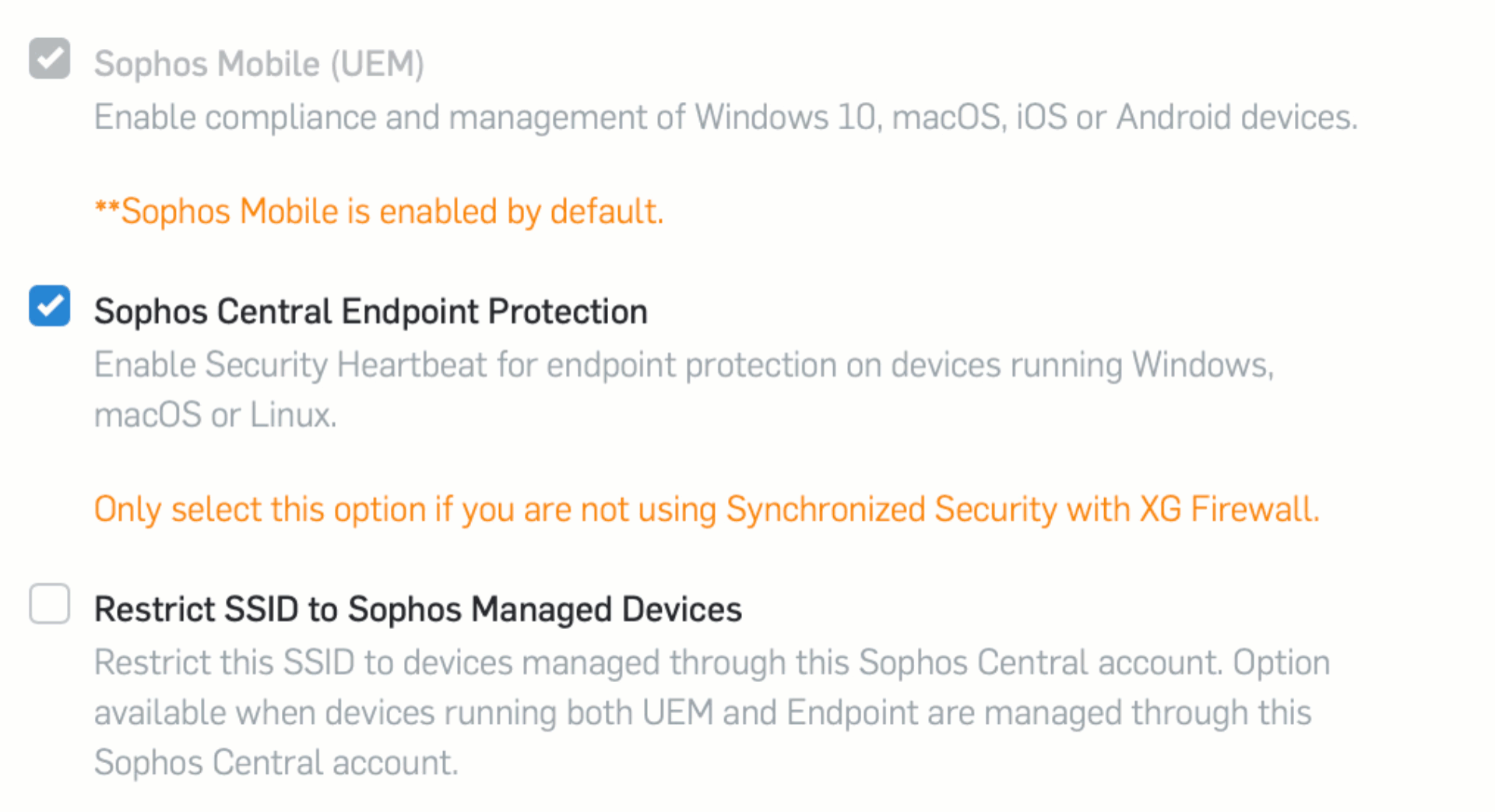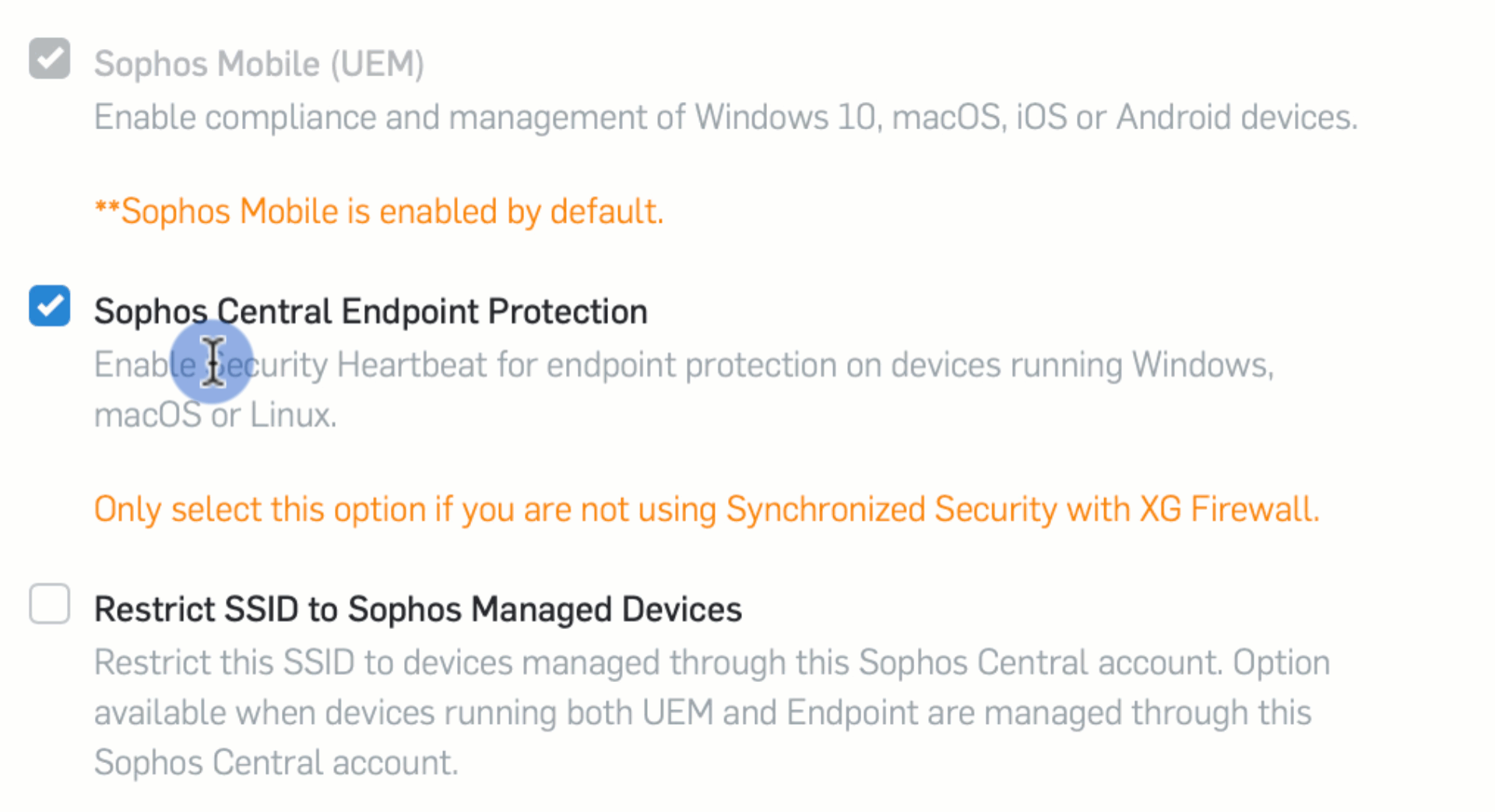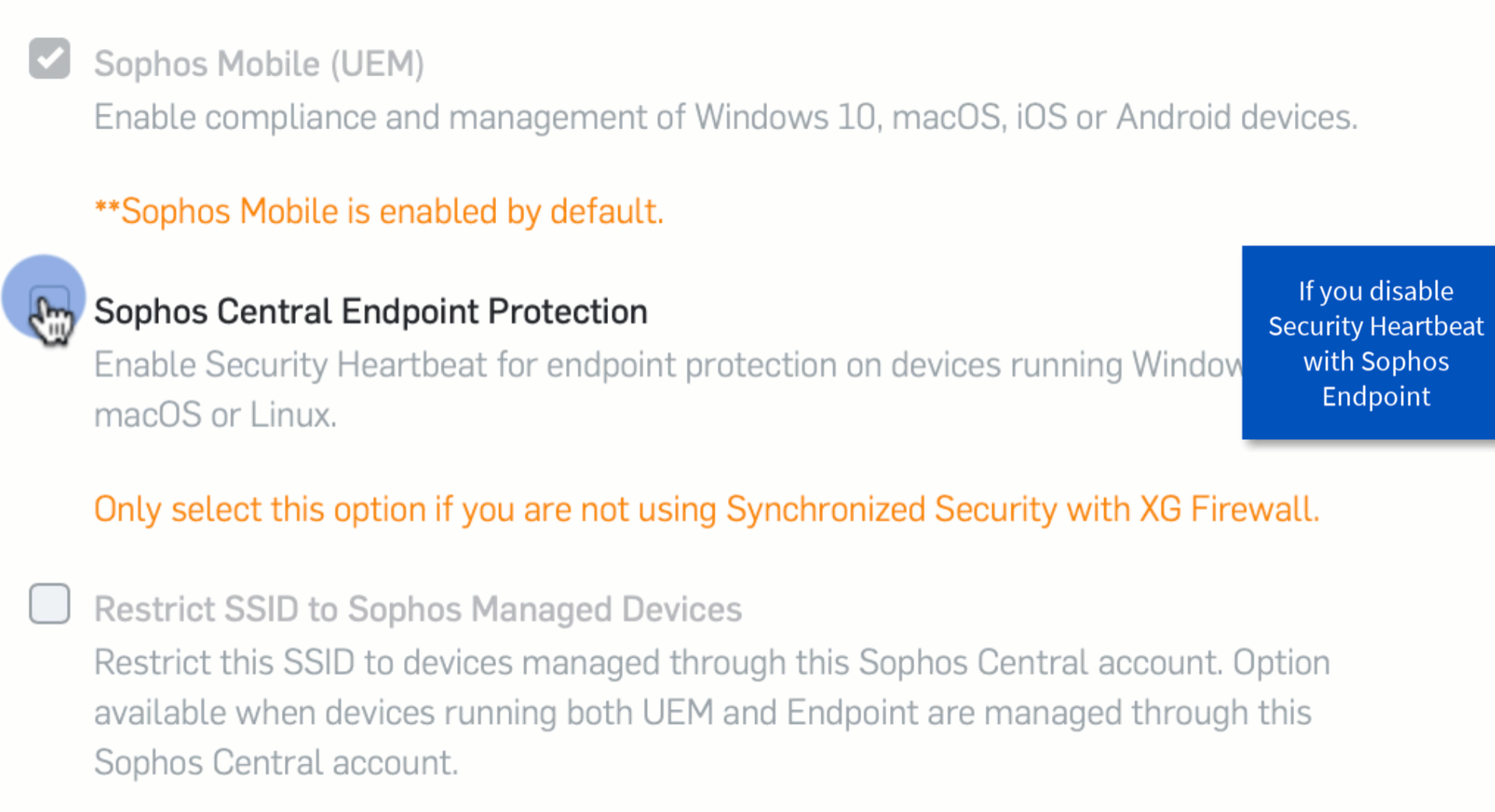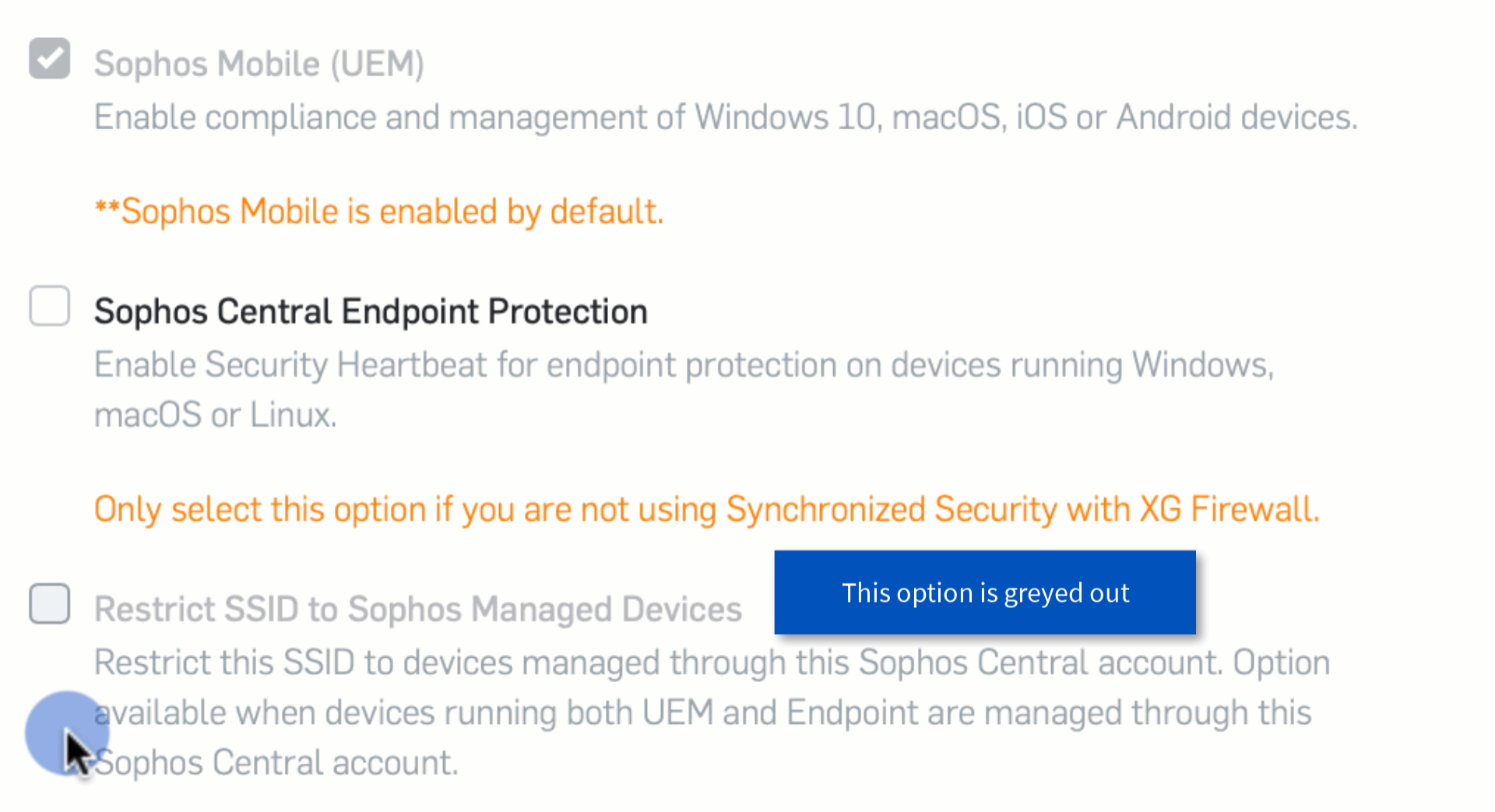
Separate Activation of Synchronized Security for Endpoint and Mobile
Even once a mobile device is managed, there is still the risk of it becoming the entry point for attacks on the network. That’s why it’s important to not only control access at the device level but also on the networks they’re connecting to, and for many mobile devices that means Wi-Fi.
Feature Recap: Sophos Wireless Synchronized Security
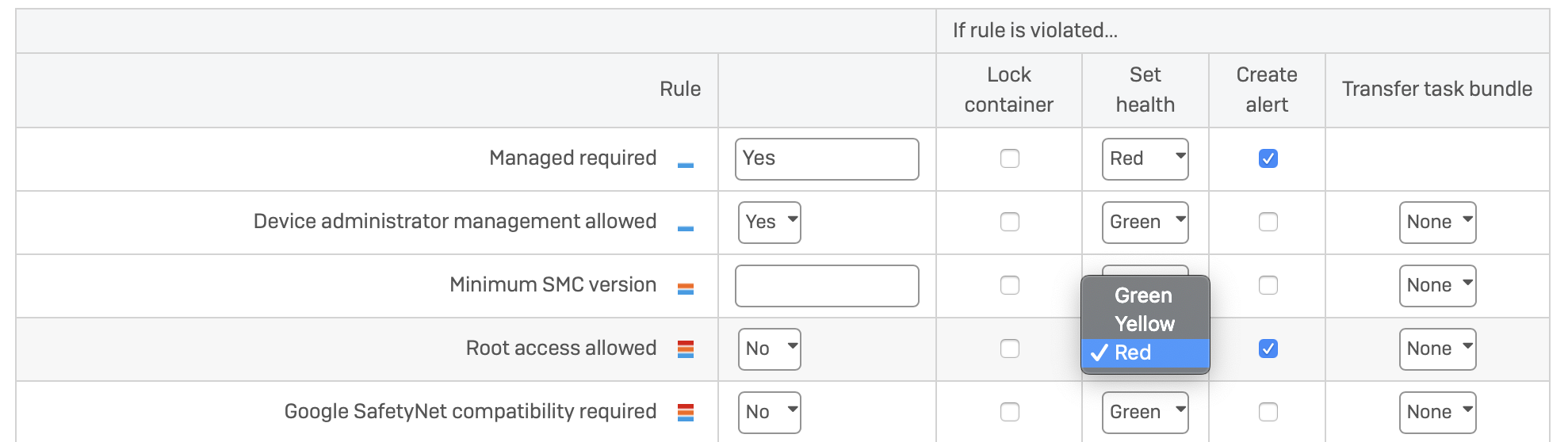
If Synchronized Security is activated in Wireless, the dashboard shows the health status of the device and if red, Wi-Fi access is denied to all but a custom list of URLs (known as a ‘walled garden’, more on this feature below).
For mobile devices the admin can set ‘Network Access Control’ rules for each compliance rule and set a green, yellow or red health status (see below).
Until now, customers already using Synchronized Security with XG Firewall and Endpoint, could not take advantage of this feature as an activation in Wireless meant the heartbeat was no longer sent to XG. We have now separated the activation, so the admin can deactivate synchronized security for Endpoint in Wireless, but the security settings used in Sophos Mobile will still be turned on (by default) and apply to any mobile devices connected via Wi-Fi and managed through the same Sophos Central account.
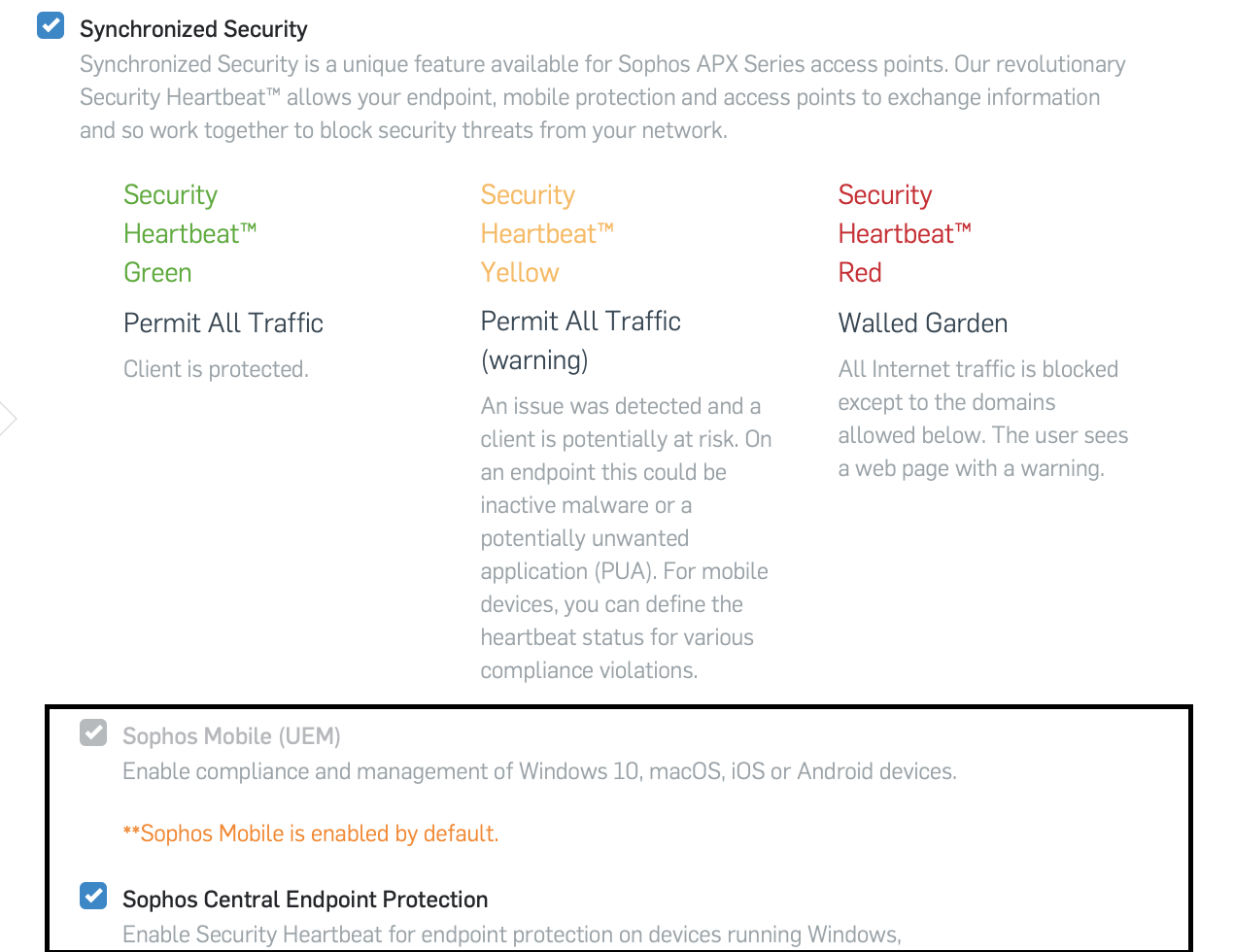
By offering this additional level of control and security, a mobile device connecting through Wi-Fi could be prevented from connected to potentially malicious web servers as part of a broader attack. Any customer who has already seen the value of synchronized security features in XG, can now add to their protection by using the integrated power of Wireless and Mobile.
Remember: this feature is only available with APX access points managed through Sophos Central.
Discovery questions:
- How do you prevent a non-compliant mobile device from connecting to your corporate Wi-Fi network?
- With Wireless + Mobile in Sophos Central this would be fully automated.
- You’re already using synchronized security for your endpoints with XG Firewall, are you able to place similar restrictions on mobile devices connecting to the Wi-Fi network?
- What visibility do you have into the health status of your mobile devices?
Restrict Wi-Fi Networks to Managed Devices
Note: This feature is only available if synchronized security is activated for both Mobile and Endpoint in Sophos Wireless.
You wouldn’t let a person you don’t trust into your home and you certainly don’t want a user on your corporate network who doesn’t deserve to be there because they don’t adhere to your security policies.
Organizations considering a transition to zero-trust are probably already looking at the different levels of trust which can be applied today, particularly in Bring-Your-Own-Device type environments. Putting a device under management means a set of rules are automatically enforced and therefore, generally implies a level of trust. The level of access a device has to a corporate Wi-Fi network can be one element of that.
In Sophos Wireless, SSIDs can now be created which are restricted to managed devices only. Management must be in the same Sophos Central account.
 Any device which connects to the SSID which is not managed will be treated in the same way as a device with a red security heartbeat, meaning that they have access to a limited, custom list of URLs. When a user attempts to access a different site, a warning page is displayed.
Any device which connects to the SSID which is not managed will be treated in the same way as a device with a red security heartbeat, meaning that they have access to a limited, custom list of URLs. When a user attempts to access a different site, a warning page is displayed.
The warning page in this instance can be customized once the SSID has been created – see image on the left – and so a company can give employees further information about how to register their device or provide a link to a website which has been whitelisted for remediation purposes.
This feature could also be used to create a walled garden, a restricted environment with access limited to a list of whitelisted URLs.
Customization of URL whitelist for red security heartbeat/walled garden status
Until now, a device with a red health status was put into a so-called walled garden, where it could only access a list of predefined URLs created by Sophos (all were *sophos.com domains). This is similar to the experience when you check into a hotel and only have access to their website until you’ve registered for full access to their Wi-Fi network.
This release adds the option to customize the URL whitelist and so give admins the opportunity to add, for example, websites required for the remediation of compliance issues, or other internal websites where further useful information about company policies or security downloads is available.
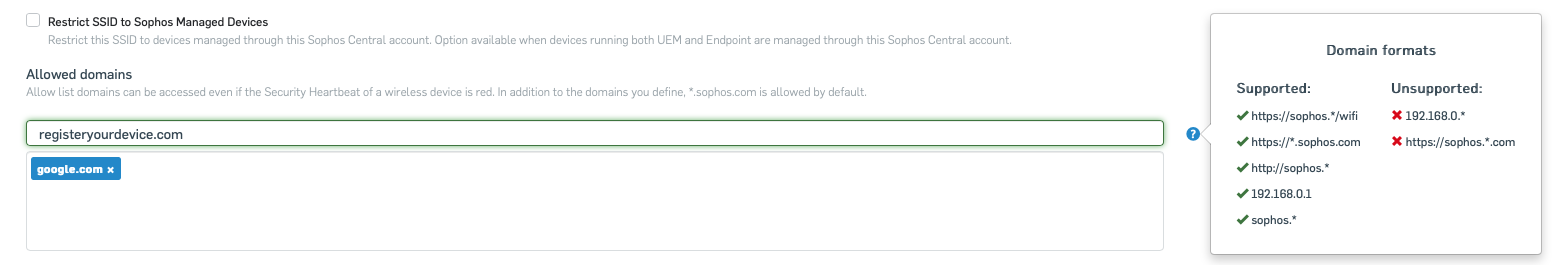
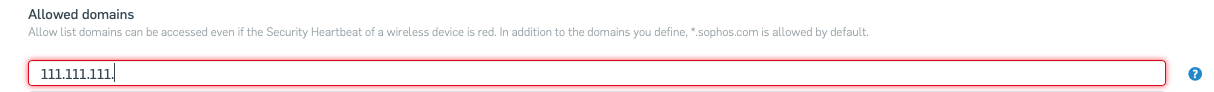
In Sophos Central, simply type in the URL or IP address and then click return. If the border of the field shows red, then the format is not supported.
User identity shown in device list for some authentication types
User identity is going to be a key part of our zero-trust strategy. If you know who’s connecting, you can apply the appropriate level of access for them.
Sophos Wireless will now show the user identity in the device list for some authentication types. Of course, those authentication types will need to involve the user having entered some form of username to gain access, such as their email address.
The supported authentication types are:
- WPA2 Enterprise
- Authentication using the Captive Portal
- Social Login
- Backend authentication
More Opportunities and What’s Coming Next
All of these features improve the general use of Sophos Wireless and open up more opportunities to position Sophos Central managed Wireless with both your XG Firewall and your Sophos Central customers.
Outdoor APX 320X
The next step for Wireless will be the introduction of the new Outdoor APX 320X in early September. This comes with a slight delay from the original plan, and you may have seen this mentioned in the price list which becomes valid today. We’ll provide more information on that very soon.