Identifying an indicator of attack is not sufficient to guarantee a healthy network, IT administrators have over the years encountered issues with inability to manage alerts and reports generated from next generation endpoint protections.
With our Sophos Intercept X Advanced with XDR solution with Detection capabilities we will be able to take you through the A-Z approach to threat response and analysis. The evolvement of Sophos XDR has extended data telemetry sources beyond endpoint and server protection, incorporating firewall, email, and other data sources. You get a comprehensive picture of your company’s cybersecurity posture, with the option to dive into specific detail when necessary.
By default, Sophos XDR offers customers 30 days of cloud storage in the Sophos Data Lake, alongside the 90 days of data that is stored directly on the device for real-time and historical searches. This enables offline access to critical devices in the case of investigating suspicious activity.
In addition to this, Sophos XDR with Detection provides a prioritized list of suspected activity and vulnerable configurations that warrant immediate attention. The prioritised list makes it easy for admins to focus on the important issues, and reduces time spent on investigating low risk events.
The Sophos XDR with Detection capability has been designed to help reduce noise in customer environments. It places scale of preference to alerts based on the risk level and hazard rate. We have discovered that having visibility to the threat on your network is good, being armed with the right technical expertise is also fantastic but it is best to have the right tool to help analyse threat risk to combat and prioritise threats. This will save the threat hunting team plenty of time and enhance their decision-making skill in combating threats, rather than enforcing the same energy on threats generally and thus losing out on issues that require immediate action.
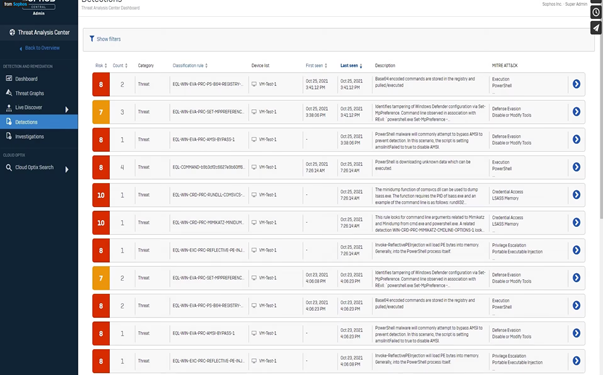
Detection classifies activities in your environment mapped against the MITRE ATT&CK framework, each detection carries a risk score, the number of times it was seen, when it was first and last seen, a description of the detection, how its mapped to MITRE ATT&CK and more.
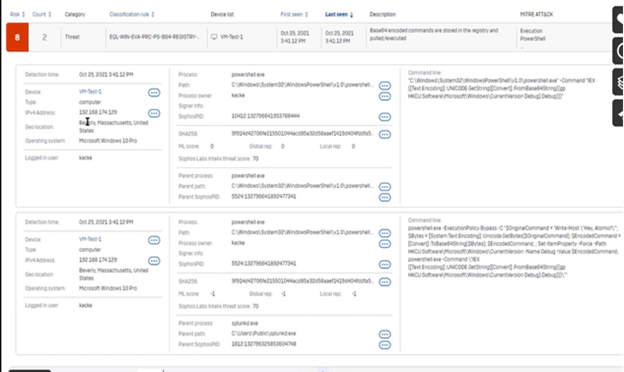
Suspected activities are ranked on a 1-10 risk scale (10 being the highest risk) highlighting a description of the detection, and how it maps to the MITRE ATT&CK framework. Additional details include the time of the event, associated processes, executed command lines, file hashes, device, user and more.
You can expand detection to see helpful contextual information, by clicking on the Device Geo location, file harsh and devices. Then you can further query, scan it, or connect to it to begin a live response session as extensive as you can analyse the harsh to further run query or look it up on virus total.
You can also generate a threat graph which shows the threat recreation of the detection step by step. This provides additional information to enable you run queries for broad troubleshooting.
It’s simple to take further action when diving into the details of a suspicious item with a context aware list (aka pivoting) of deeper research alternatives and immediate actions that may be performed, such as conducting more search activities or opening a Live Response session.
This broad set of information gives admins vital context, making it easy to quickly understand if a suspicious item requires action and then easily take any necessary remedial steps.
Next Steps
The Sophos XDR Detections dashboard is now available for all Intercept X Advanced with XDR and Intercept X Advanced for Server with XDR customers.
You can also check out the below videos:
- Overview Video: https://vimeo.com/642818665
- Technical Video: https://vimeo.com/642727668
If your customers don’t have a Sophos Central account they can start trials for their endpoints and servers on the Sophos.com website.