 The latest operating system from Apple, macOS11 Big Sur, has arrived and it brings with it a few significant architecture modifications. In this article, we will take a look at these changes, as well as some of the things you might consider doing to automate much of the deployment of Intercept X on macOS.
The latest operating system from Apple, macOS11 Big Sur, has arrived and it brings with it a few significant architecture modifications. In this article, we will take a look at these changes, as well as some of the things you might consider doing to automate much of the deployment of Intercept X on macOS.
These changes started to appear with macOS Catalina (10.15) – Apple is beginning to deprecate the use of system wide kernel extensions in favour of user space system extension APIs. This allows software like network extensions and endpoint security solutions to extend the functionality of macOS without requiring kernel-level access.
An interesting third party review of some of the most significant changes in the last decade Apple have recently introduced can be found here.
Unfortunately, we didn’t have a GA version of Intercept X for Mac available on the first day of release. The good news is that we now have an Early Access Program (EAP) available in Central, whereby customers can nroll devices running macOS11 in order to receive a pre-release version of Sophos Endpoint v10.0.2.
TIP: As you can appreciate, we don’t typically recommend using EAP (pre-release) software on a production system. If you would like to prevent users from upgrading to BigSur AND if you or your customer are using Sophos Endpoint, then it’s worth noting that the SophosLabs have added an Application Control detection for the Big Sur installer. This means that you can control its rollout by blocking the application – the installer is classified as a “System Tool”.
Most of you are probably aware of the process on how to join an EAP and then enroll devices, however if you would like some info on this process click here. Typically, we don’t make EAPs available to Sophos Central MSP accounts, however given that some customers may be purchasing new Apple hardware that comes pre-shipped running Big Sur, we have extended the EAP to MSP customers too.
About new hardware, the following Macintosh models (at the time of writing) use the new Apple M1 ARM-based system chipset:
- MacBook Air (M1, 2020)
- Mac mini (M1, 2020)
- MacBook Pro (13-inch, M1, 2020)
Sophos Intercept X for Mac does not natively support this new chipset; however, it can be made to work using a piece of backwards compatibility software called Rosetta 2. This software needs to be installed on the Mac before joining it to the EAP and it updating to 10.0.2. More info on this process is also covered in the EAP community post above.
On testing the deployment of Intercept X on a brand new macOS11 device, I found the installation routine quite user intensive with several prompts required to allow permissions etc. before a complete protected state could be achieved.
There are several things that can be done to reduce these prompts, specifically using an MDM provider (such as Sophos Mobile or JAMF) to essentially pre-trust extensions using the Sophos ‘Teams ID’ of 2H5GFH3774. This is a trusted ID that is used in the development of Sophos code, to automatically whitelist our software:
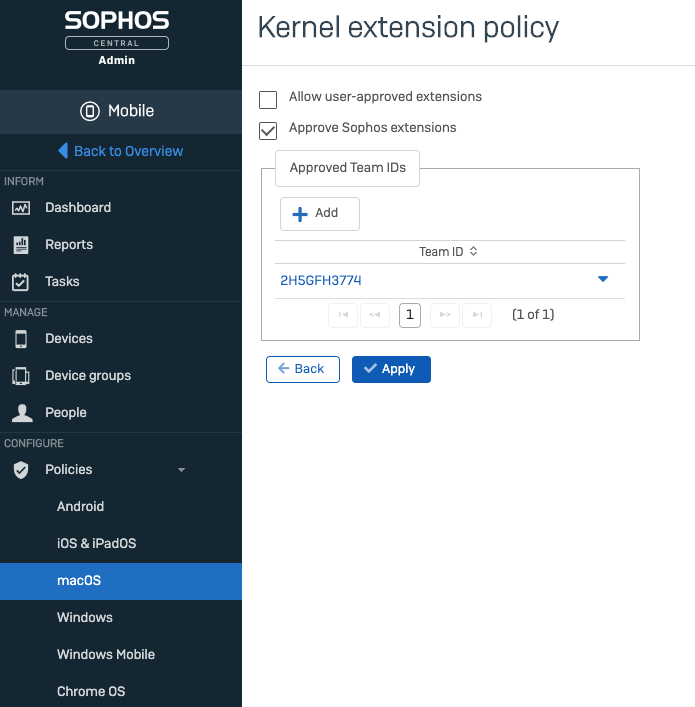
I found that this configuration made the deployment of Intercept X for Mac on macOS Catalina and older, virtually ‘silent’. There were still some prompts that required user interaction when deploying on Big Sur, however this will still down on the amount of interaction required without any applied MDM settings.
Our wonderful professional services team have also created a number of scripts to use with JAMF to automate deployment on Macs. Info on this can be found here.
Expect to see some more information in the new year, once a GA version of 10.0.2 for Mac is available, on how to automate the deployment further.