Chasing down attacks through cloud environments can be tough if you don’t know what to look out for, and sometimes, even if you do. That’s why we’re pleased to announce the integration of Cloud Optix data for AWS environments into the Sophos Extended Detection and Response (XDR) platform, with easy-to-follow queries to help while investigating incidents in AWS.
Improving threat detection and response in AWS with Sophos XDR
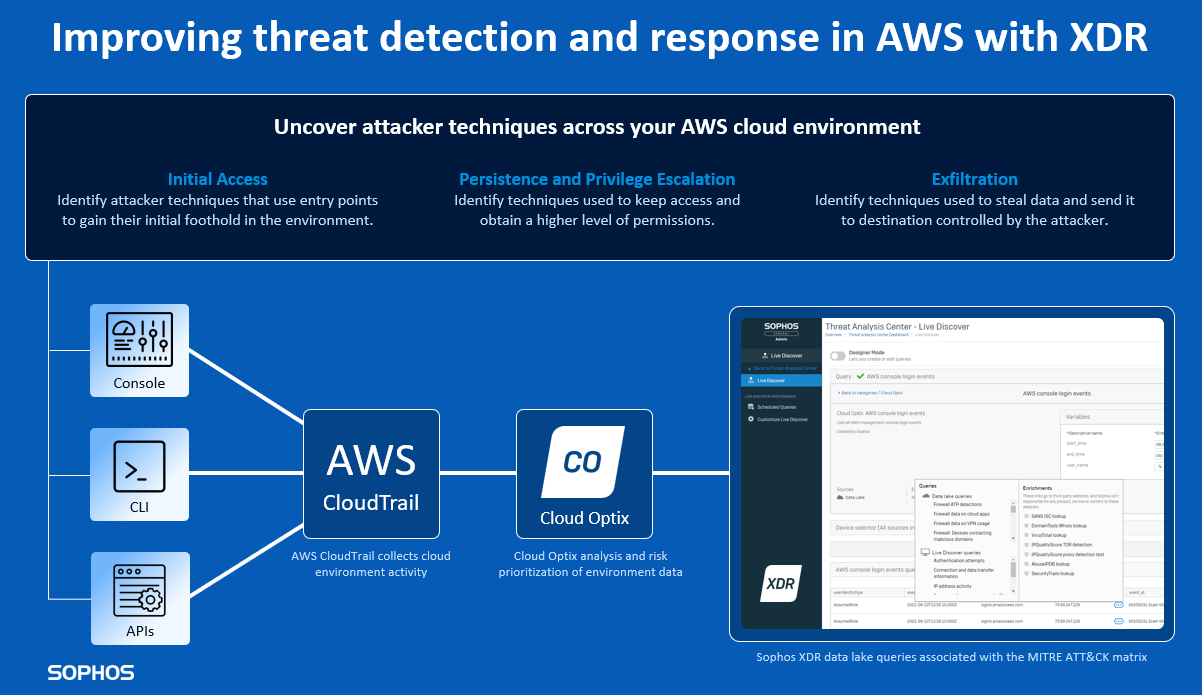
Thanks to its integration with the AWS CloudTrail service, Sophos Cloud Optix can collect and analyze data from across an organization’s AWS environment. This allows security teams to efficiently identify attacker techniques used to gain entry, maintain access, and exfiltrate data. Activity that could otherwise be missed.
Breaking down this Sophos XDR release
Extending your data sources
Data sources are critical to an effective XDR strategy. Sophos XDR goes beyond the endpoint, pulling in rich virtual network, SaaS email, and cloud workload data. This is now further enhanced with AWS cloud environment data sources from Cloud Optix to provide greater visibility of attacker tactics within your cloud environment.
Use extended telemetry to detect activity
Using Cloud Optix data from AWS CloudTrial in Sophos XDR, security teams can investigate AWS cloud environment API, CLI, and management console activities, using fully customizable and pre-written SQL queries associated with the MITRE ATT&CK IaaS matrix including Initial Access, Persistence, Privilege Escalation, and Exfiltration tactics.
Investigate and respond to incidents with greater accuracy
Helping teams see the bigger picture during investigations from one central console helps them to quickly identify risk and possible compromise. Cloud Optix data in Sophos XDR unlocks more value from AWS CloudTrail alerts and helps analysts more efficiently query the attack paths an attacker may take once they gain access to an AWS environment.
Examples of Cloud Optix detections include multi-factor authentication (MFA) being disabled for an AWS IAM User, changes to AWS EC2 instance snapshot attributes that could allow resources to be made publicly available, or data exfiltration from AWS EC2 instances. Teams can then pivot in the same console to enrich their investigations by running additional queries such as IP address activity, ATP detection, and third-party threat intelligence lookups to act where needed.
Getting started
To get started, your customers will need Intercept X Advanced for Server or Endpoint with XDR, and Sophos Cloud Optix Advanced with AWS CloudTrail enabled.
You can find out more about how Cloud Optix enables IT teams to proactively protect cloud environments at Sophos.com/Cloud-Optix. From there you can try for free, resell through AWS Marketplace, and learn more about Sophos XDR for cloud workloads.