Integrating data from the Sophos cloud security posture management solution, Cloud Optix, Sophos XDR enables you as a Sophos partner to detect, assess and harden cloud workloads and user access against security misconfigurations and vulnerabilities.
New Cloud Optix data sources in Sophos XDR now allow you to easily investigate AWS, Azure and GCP cloud environment API, CLI, and management console activities. Using fully customizable and pre-written SQL queries you can uncover initial access attempts on the environment via compromised roles, as well newly created user roles and resources indicating persistence within the environment, and privilege escalation and exfiltration tactics shown by attackers.
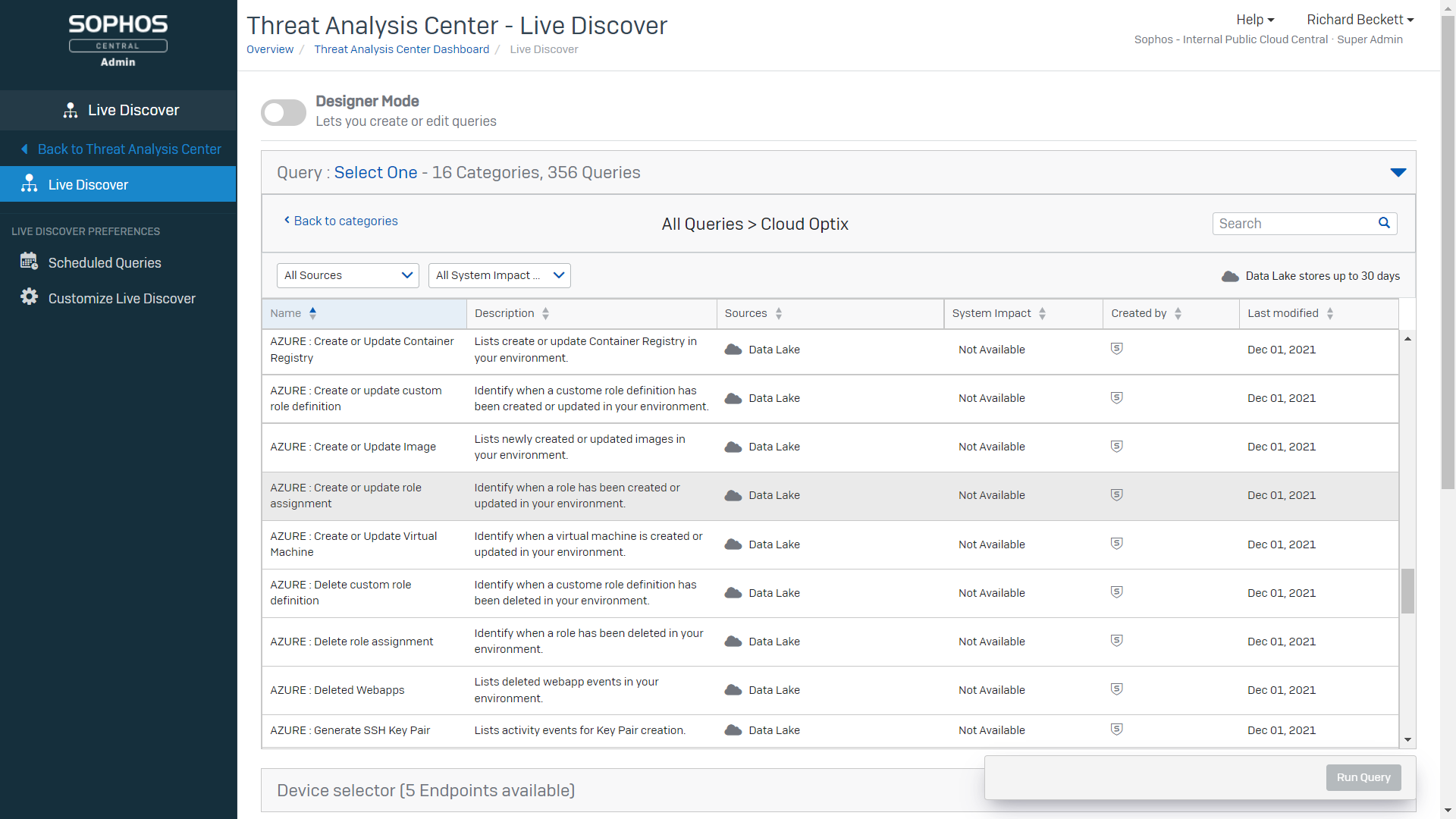
Using Cloud Optix findings as an indicator of compromise, we help you pivot using the Sophos XDR data lake to investigate workload vulnerabilities using Sophos Intercept X for Server workload protection agents running on those workloads. Examples include the detection of compute workload resources with ports, such as RDP or SSH exposed to the internet. In this scenario, Cloud Optix, alerts you to these access vulnerabilities, and Sophos XDR allows you to quickly pivot investigations to identify the number of authentication attempts on those instances, and any successful attempts made. You can then act confidently, to remove access and prevent a breach, with Cloud Optix providing guided remediation instructions to reduce your mean time to resolve (MTTR) vulnerabilities.
This connected picture of multi-cloud security from one central console differentiates your cloud security practice, and helps security teams see the bigger picture during investigations – making it easy to quickly identify risk and proactively prevent security incidents.
More Cloud Optix enhancements
This latest update to Sophos Cloud Optix also includes a range of additions to enhance cloud security monitoring and compliance response for your customers:
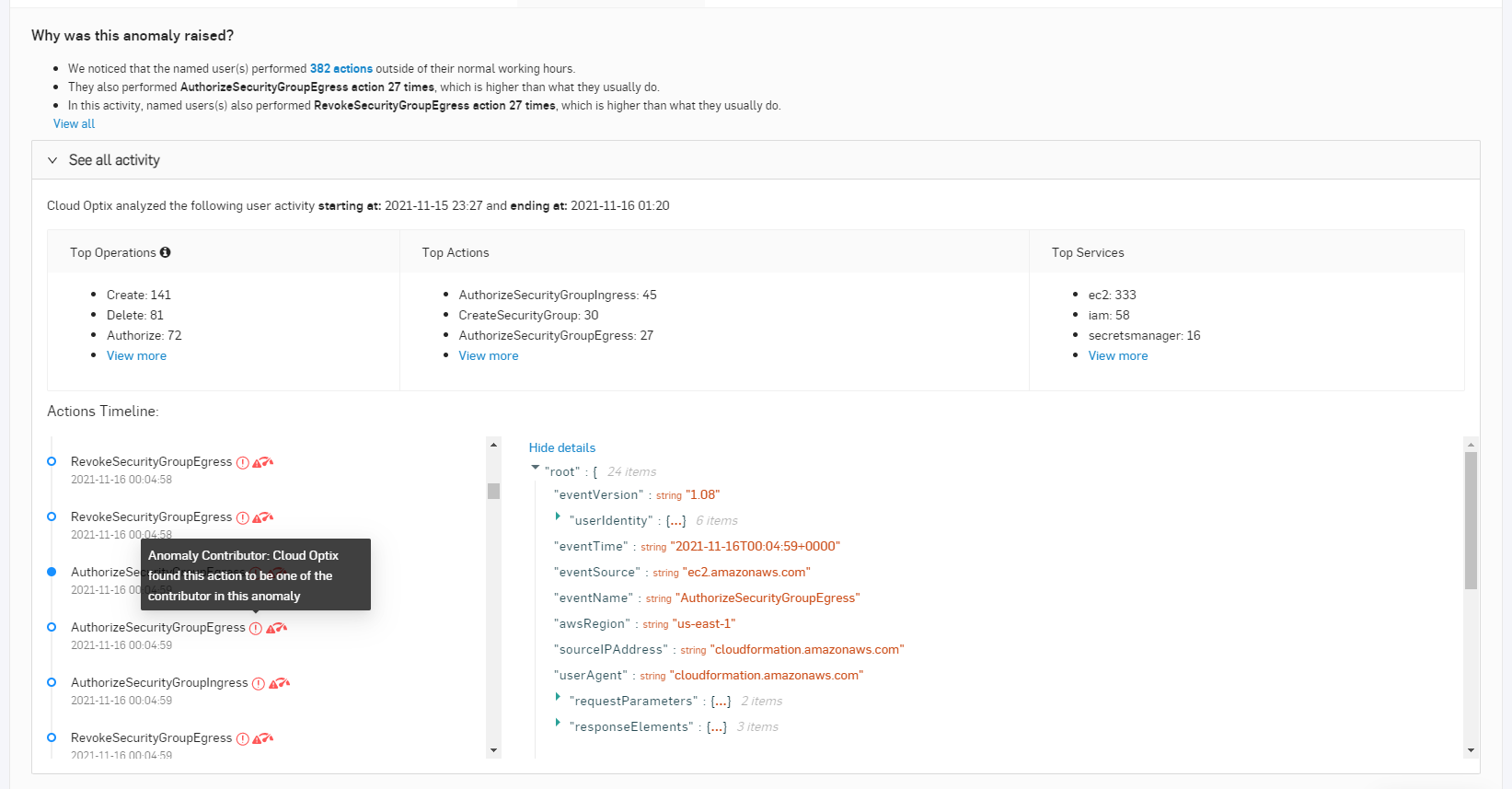
AWS Activity Anomalies – New SophosAI models continuously analyze AWS CloudTrail user activity logs. This allows Cloud Optix to build a picture of individual user role activity to identify both accidental changes as well as malicious activity from compromised roles. It brings AWS CloudTrail events to life in a clear and detailed timeline view of user activities, identifying high risk anomalies such as actions performed outside of normal working hours as well as those never performed before.
With this update you can dramatically shrink alert totals for security teams and help them focus on investigating high-risk patterns of behavior that could lead to a security incident in a fraction of the time that it took them before.
Multiple Jira Integration Instances – Now add multiple Jira Integration instances to a Cloud Optix account. Each cloud environment will be linked to one Jira instance. This could be a separate Jira Instance per environment, or a common Jira instance shared with many environments.
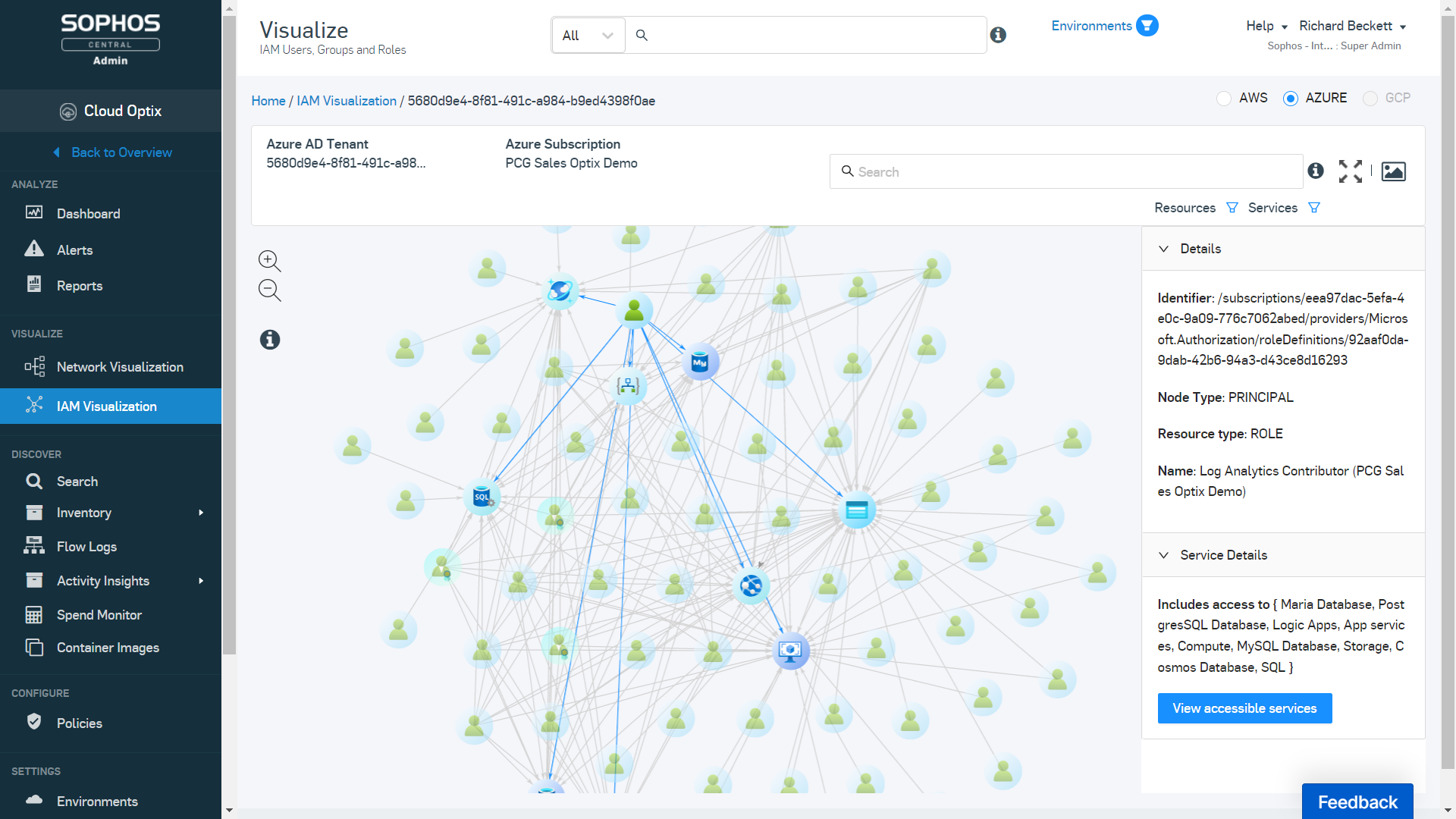
Azure IAM Visualization – Visualize the relationships between IAM Roles, IAM Users, and Services in Azure to simplify the management of complex, interwoven IAM roles for multiple Azure subscriptions and Azure AD.
Custom Policy Alerts – Now create custom alerts based on Cloud Optix advanced search queries. Future security benchmark scans will then raise alerts in Cloud Optix when the criteria of the query is met.
These latest updates and a recap of all Cloud Optix enhances is available here. To find out more about Sophos Cloud Security Provider Partner Program and adding Cloud Optix to your portfolio as a Sophos Partner, visit www.sophos.com/csp, or find the CSP Hub in the Sophos Partner Portal.